
OpenSSH 7.8 is out. It includes a fix for the usernameenumeration vulnerability; additionally, the default format for theprivate key file has changed, support for running
- Openssh 7.9p1
- Openssh 7.2p2 Vulnerabilities
- Openssh 7.2p2
- Openssh 7.6p1
- Openssh 7.9 Vulnerability
- Openssh 7.4 Exploit
OpenSSH 7.0 and greater similarly disables the ssh-dss (DSA) public key algorithm. It too is weak and we recommend against its use. Which is no more detailed than the 'inherit weakness' from the announce. I did not find any published explanation about these weaknesses except some unsubstantiated weaselling that talks of 'recent discoveries. The SSH server running on the remote host is affected by a file creation restriction bypass vulnerability. Description According to its banner, the version of OpenSSH running on the remote host is prior to 7.6. It is, therefore, affected by a file creation restriction bypass vulnerability related to the 'processopen' function in the file 'sftp. How can I upgrade OpenSSH 7.4 to 7.8 on RHEL Machines? Is it possible to upgrade the installed OpenSSH Packages to their upstream release versions? Red Hat Enterprise Linux (RHEL) 7, 8; Subscriber exclusive content. A Red Hat subscription provides unlimited access to our knowledgebase of over 48,000 articles and solutions.
Introduction to OpenSSH The OpenSSH package contains ssh clients and the sshd daemon. This is useful for encrypting authentication and subsequent traffic over a network. The ssh and scp commands are secure implementions of telnet and rcp respectively. This package is known to build and work properly using an LFS-7.10 platform. OpenSSH.4 - agent Protocol Arbitrary Library Loading. Remote exploit for Linux platform.
ssh setuid roothas been removed, a couple of new signature algorithms have been added, andmore.| From: | Damien Miller <djm-AT-openbsd.org> |
| To: | lwn-AT-lwn.net |
| Subject: | Announce: OpenSSH 7.8 released |
| Date: | Thu, 23 Aug 2018 18:46:01 -0600 (MDT) |
| Message-ID: | <e0a2ea1caf6c3409@openbsd.org> |
Openssh 7.9p1
(Log in to post comments)Private key encryption change
Posted Aug 24, 2018 21:35 UTC (Fri) by tialaramex (subscriber, #21167) [Link]
For the key format change (which anybody reading LWN should probably go fix now, takes like two minutes) It seems fairly reasonable to credit:https://latacora.singles/2018/08/03/the-default-openssh.html
I'm not clear on whether it's Latacora policy not to credit individuals on that blog, or in fact Latacora is primarily a single person, or what.
But it seems like the overwhelming responses to it were:
1. Well, but I don't really see how this is worse than plaintext? Oh, I see. Well, I guess that's not great news.
2. Why the heck doesn't OpenSSH do this by default for, say, the last several years?
3. OK, I buy your explanation for why some people won't want this, but, again, _default_? Why have a default that supports crazy people but makes everybody else's security worse?
All of which screams 'Change the default' or preferably 'Go back in time, and change the default weeks ago' but time machines are not available to the OpenSSH team.
Private key encryption change
Openssh 7.2p2 Vulnerabilities
Posted Aug 25, 2018 4:49 UTC (Sat) by k8to (subscriber, #15413) [Link]
Private key encryption change

Posted Aug 26, 2018 1:44 UTC (Sun) by gus3 (subscriber, #61103) [Link]
But that future copy of me left another copy of the machine somewhere else.Which simplifies the solution domain, but renders the problem domain much more complex. Kind of like grep and Perl.
Private key encryption change
Posted Aug 25, 2018 13:04 UTC (Sat) by ScienceMan (subscriber, #122508) [Link]
Just a short note to endorse the above in its entirety. For me it took a few more minutes to read the documentation and the post, try out 'ssh-keygen -p -o -f KEYFILE' on an example RSA test key to verify that it did as advertised let me leave the legacy RSA public key untouched while upgrading the private key to the openssh new default format, verify in a test setting that I could use this with any key agent I needed to fire up, and thus resolve to upgrade all of my legacy keys using this procedure.People reading this who need to keep their existing RSA public keys working until they can look into other methods while avoiding having nasty hackable private keys laying around should do this right away. Read the documentation if you want to find out what this is doing, and compare the public and private keys before and after the procedure if you want peace of mind that you have in fact done a Good Thing (TM). You might as well upgrade your password to something longer and less guessable along the way.
Private key encryption change
Posted Aug 27, 2018 10:44 UTC (Mon) by gdt (subscriber, #6284) [Link]
You might as well upgrade your password to something longer and less guessable along the way.
Can I suggest that passwords are no longer fit for purpose. Even 40-odd bits of randomness for a 'poor' password pushes human limits (eg: IRYgxNV) and 80-odd bits easily exceeds those limits (eg: X7g6zCi2xqKbKzV9). I'm not that comfortable with security recommendations which require beyond-human performance to meet, especially if those recommendations then implicitly criticise people for being human.
Could I suggest that we begin to recommend hardware tokens for authentication? And where services don't support tokens themselves that we suggest a password manager and that access to it be secured by a hardware token?
I've got hopes for U2F FIDO2 as a primary source of authentication which displaces passwords. We'll see.
Private key encryption change
Posted Aug 27, 2018 10:53 UTC (Mon) by cagrazia (subscriber, #124754) [Link]
> Even 40-odd bits of randomness for a 'poor' password pushes human limits (eg: IRYgxNV) and 80-odd bits easily exceeds those limits (eg: X7g6zCi2xqKbKzV9)Relevant XKCD: https://xkcd.com/936/
Private key encryption change
Posted Aug 27, 2018 11:06 UTC (Mon) by gdt (subscriber, #6284) [Link]
I would suggest the ability to choose 'four random common words' is also beyond human capability. There's no shortage of psychology papers suggesting that human can't make a random choice from 1000-or-so items, yet the xkcd algorithm relies upon such an ability for its strength.
Private key encryption change
Posted Aug 27, 2018 12:06 UTC (Mon) by karkhaz (✭ supporter ✭, #99844) [Link]
Openssh 7.2p2
Private key encryption change
Posted Aug 27, 2018 18:07 UTC (Mon) by micka (subscriber, #38720) [Link]
Private key encryption change
Posted Aug 27, 2018 17:19 UTC (Mon) by brouhaha (subscriber, #1698) [Link]
Private key encryption change
Posted Aug 27, 2018 20:42 UTC (Mon) by epa (subscriber, #39769) [Link]
Private key encryption change
Posted Aug 27, 2018 18:40 UTC (Mon) by brunowolff (guest, #71160) [Link]
That has not been my experience. I've found for a password that I use (i.e. type) multiple times a day, I can remember a password with 130+ bits of entropy (e.g. Q'Z@b,WQk!#x?i#gZVv) and even remember it after short breaks (e.g. a week) from using it.
Private key encryption change
Posted Aug 28, 2018 12:46 UTC (Tue) by ledow (guest, #11753) [Link]
Can you remember two passwords of half the strength required?Congratulations you can remember a single password of the strength required.
Human memory is not yet the limiter. But if it was then a password manager would be in order, protected by something the human has / knows. Not dumbing down to the humans.
Private key encryption change
Posted Aug 28, 2018 8:31 UTC (Tue) by joib (subscriber, #8541) [Link]
As a heads-up, using the new-style encrypted private keys breaks gnome-keyring (at least the version in Ubuntu 16.04, don't know if it has been fixed since). So if you get error messages when trying to ssh to some host likesign_and_send_pubkey: signing failed: agent refused operation
Permission denied (publickey,gssapi-keyex,gssapi-with-mic).
then it means the problem is that gnome-keyring doesn't understand the private key. One solution is to disable gnome-keyring and instead use ssh-agent.
Private key encryption change
Posted Aug 28, 2018 10:45 UTC (Tue) by tialaramex (subscriber, #21167) [Link]
Private key encryption change
Posted Aug 28, 2018 19:12 UTC (Tue) by joib (subscriber, #8541) [Link]
Oh, great, that should(?) fix other long-standing issues with gnome-keyring as well, such as lack of support for ECDSA or Ed25519 keys.FWIW, it seems the relevant bug report is https://bugzilla.gnome.org/show_bug.cgi?id=775981
OpenSSH 7.8 released
Posted Aug 27, 2018 16:03 UTC (Mon) by frostsnow (subscriber, #114957) [Link]
Openssh 7.6p1
OpenSSH is the open-source version of the Secure Shell (SSH) tools used by administrators of Linux and other non-Windows for cross-platform management of remote systems.OpenSSH has been added to Windows as of autumn 2018, and is included in Windows 10 and Windows Server 2019.
SSH is based on a client-server architecture where the system the user is working on is the client and the remote system being managed is the server.OpenSSH includes a range of components and tools designed to provide a secure and straightforward approach to remote system administration, including:
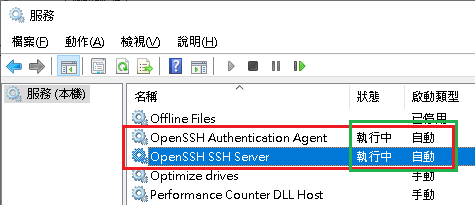
- sshd.exe, which is the SSH server component that must be running on the system being managed remotely
- ssh.exe, which is the SSH client component that runs on the user's local system
- ssh-keygen.exe generates, manages and converts authentication keys for SSH
- ssh-agent.exe stores private keys used for public key authentication
- ssh-add.exe adds private keys to the list allowed by the server
- ssh-keyscan.exe aids in collecting the public SSH host keys from a number of hosts
- sftp.exe is the service that provides the Secure File Transfer Protocol, and runs over SSH
- scp.exe is a file copy utility that runs on SSH
Documentation in this section focuses on how OpenSSH is used on Windows, including installation, and Windows-specific configuration and use cases. Here are the topics:
Openssh 7.9 Vulnerability
Additional detailed documentation for common OpenSSH features is available online at OpenSSH.com.
Openssh 7.4 Exploit
The master OpenSSH open source project is managed by developers at the OpenBSD Project.The Microsoft fork of this project is in GitHub.Feedback on Windows OpenSSH is welcomed and can be provided by creating GitHub issues in our OpenSSH GitHub repo.
